WAppEx is an integrated Web Application security assessment and exploitation platform designed with the whole spectrum of security professionals to web application hobbyists in mind. It suggests
a security assessment model which revolves around an extensible
exploit database. Further, it complements the power with various tools
required to perform all stages of a web application attack.
Updates in 2.0
Updates in 2.0
- Auto-detect feature deleted from exploits
- Browser tool deleted
- Exploits and payloads view changed
- Exploit Database with the following features added:
- New script syntax and structure
- Searching, selecting, and executing of exploits.
- Add/remove database entries (exploits or payloads)
- Add exploits or payloads to the database using either the Exploit Wizard or the script file
- Batch testing of multiple targets against multiple exploits
- Execute multiple instances of one or more payloads (for every running exploit) simultaneously.
- Following tools added:
- Manual Request
- Dork Finder
- Exploit Editor
- Hidden File Checker
- Neighbor Site Finder
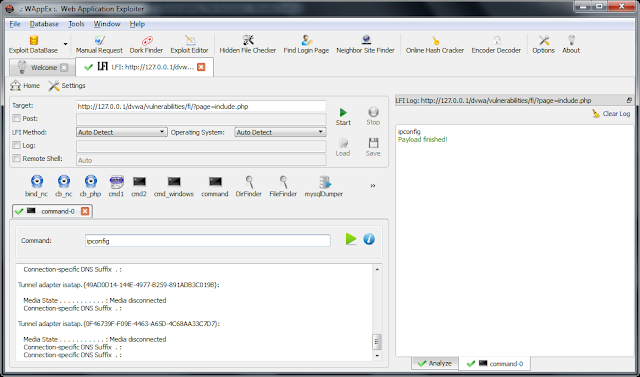
- Local File Inclusion analyzer script updated
- 24 new payloads for LFI, RFI, and PHP Code Execution vulnerabilities added:
- Directory Explorer
- CodeExec Bind
- 3 connect-back shells
- Code Execution
- MySQL Dump
- ServerInfo
- 4 command execution payloads
- Bug-fixes:
- Find Login Page crashed on start
- Problem with software registration
- Stop button did not work when retrieving data from SQL server
- Problem with saving SQL results
- Crashed when closing Find Login Page
- Status icons were not displayed properly in exploit tabs
The full list features is as below:
- An exploit database covering a wide range of vulnerabilities.
- A set of tools useful for penetration testing:
- Manual Request
- Dork Finder
- Exploit Editor
- Hidden File Checker
- Neighbor Site Finder
- Find Login Page
- Online Hash Cracker
- Encoder/Decoder
- Execute multiple instances of one or more exploits simultaneously.
- Execute multiple instances of one or more payloads (for every running exploit) simultaneously.
- Test a list of target URL’s against a number of selected exploits.
- Allows you to create your own exploits and payloads and share them online.
- A number of featured exploits (6) and payloads (39) bundled within the software exploit database:
- Testing and exploiting of Local File Inclusion vulnerabilities
- Testing and exploiting of Local File Disclosure vulnerabilities
- Testing and exploiting of Remote File Inclusion vulnerabilities
- Testing and exploiting of SQL Injection vulnerabilities
- Testing and exploiting of Remote Command Execution Inclusion vulnerabilities
- Testing and exploiting of Server-side Code Injection vulnerabilities
0 comments: